Entropy has been described as the measure of disorder of a system. The Second Law of Thermodynamics, as defined by Rudolf Clausius, states that the ‘Entropy of the universe tends to a maximum’, which means that the universe is heading towards maximum entropy, or maximum disorder. Entropy can be seen in everyday life, ice melts, metal rusts and food decays. In these cases, it is irreversible, you cannot un-melt ice, or un-rust metal or un-decay food. However, it is possible to slow down entropy. For example, you can refreeze water, treat bare metal and preserve food in a fridge or…Continue readingSecurity knowledge entropy
Category: DevSecOps
Posts that focus mainly on DevSecOps practices
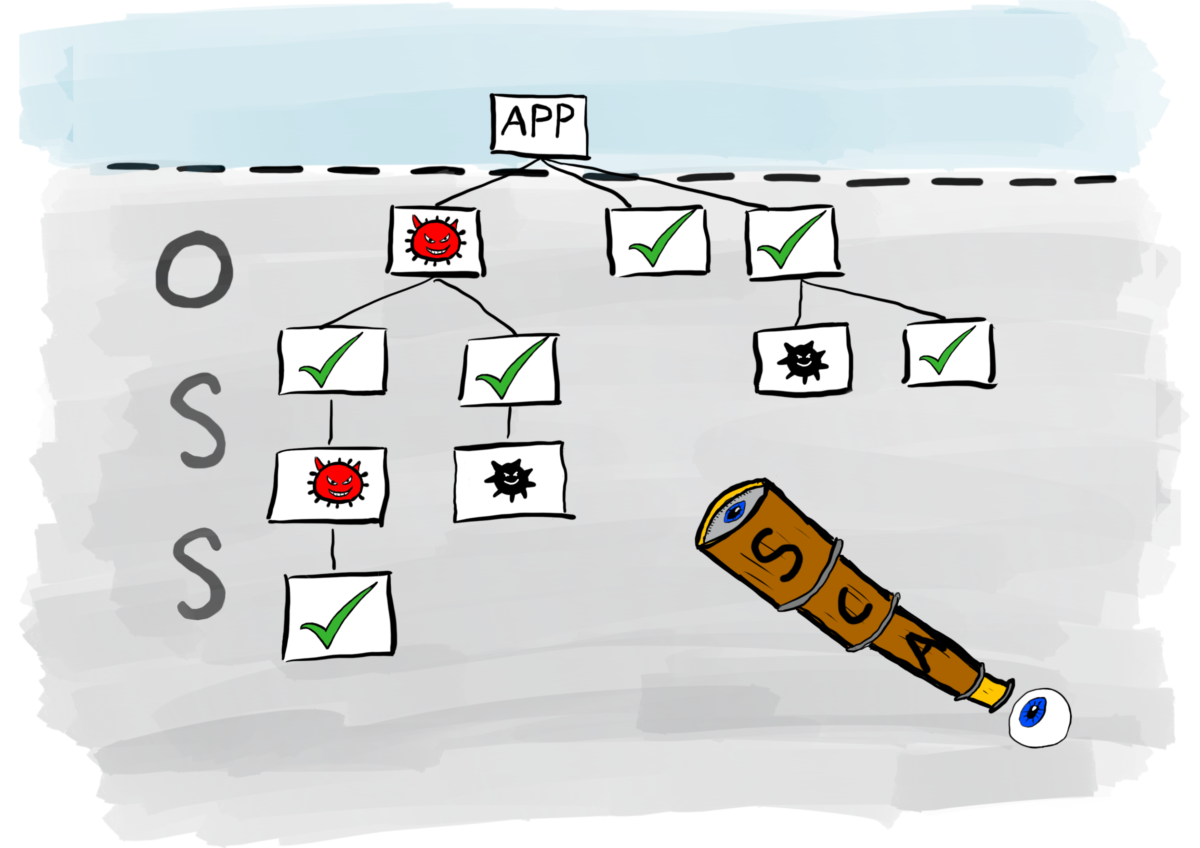
In this final instalment of articles exploring security test automation, I take a closer look at Software Composition Analysis (SCA). Open source software has grown considerably over the last few years. As engineers struggle with the writing of code that meets ever-increasing demands of the business, they do not want the distraction of writing logic to integrate those business rules into the architecture of the application. Instead, they want to use code that already does boring stuff so they can focus on adding value to their products and delivering solutions faster. The result is the proliferation of open source software…Continue readingSecurity test automation part 5: SCA
In previous articles, I wrote about the Application Security Testing tools SAST, DAST and IAST, which are designed to help engineers fix problems during the development lifecycle. In this article, I write about a technology designed to protect applications in a production environment. This technology is known as Runtime Application Self-Protection (RASP). Once an application has been deployed into a production environment, the level of real-time protection moves from proactive preventative measures associated with developing secure products, to reactive remedial measures. For example, traffic to your applications can be monitored by Web Application Firewalls (WAF) for potentially malicious activity and…Continue readingSecurity test automation part 4: RASP
In my previous two articles in this series on security test automation, I gave a brief insight into SAST and DAST. In this article I take a closer look at Interactive Application Security Testing (IAST), a relative newcomer to the security test automation scene. The key difference between IAST and the two previous types of application security testing is found in how the tools interact with the products being tested. SAST and DAST are active tools: in order for them to scan code, they need to be triggered either from the Integrated Development Environment (IDE), or from within the CI/CD…Continue readingSecurity test automation part 3: IAST
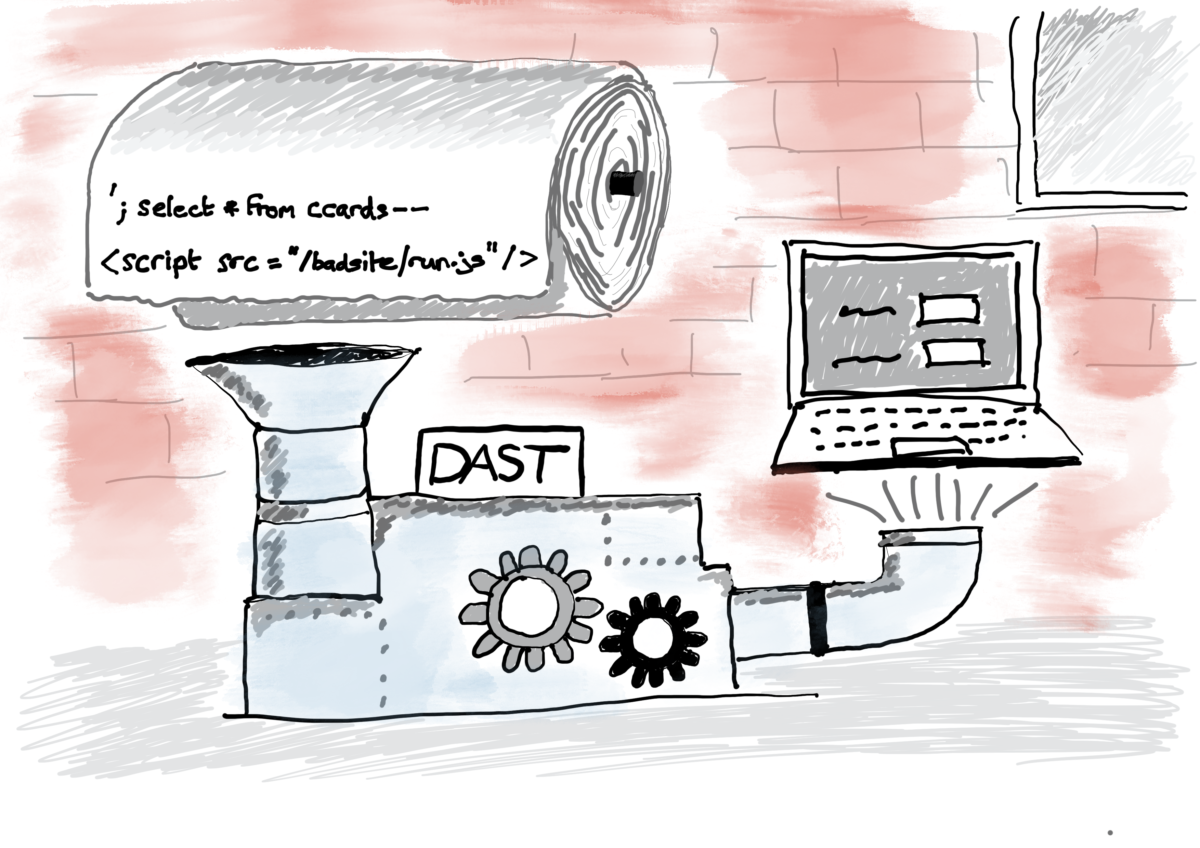
In part one of this series of articles, I wrote about Static Application Security Testing (SAST). In this second part, I turn my attention to Dynamic Application Security Testing (DAST). Unlike SAST which analyses static application source code, DAST analyses the application dynamically while it is running. Immediately, this pushes the operation of the dynamic analysis tool further right along the delivery pipeline than its static counterpart. Ideally, it needs to do its work after the application code has been integrated and is ready for functional testing. DAST has evolved over the years. When I first came across it, vendors offered a…Continue readingSecurity test automation part 2: DAST
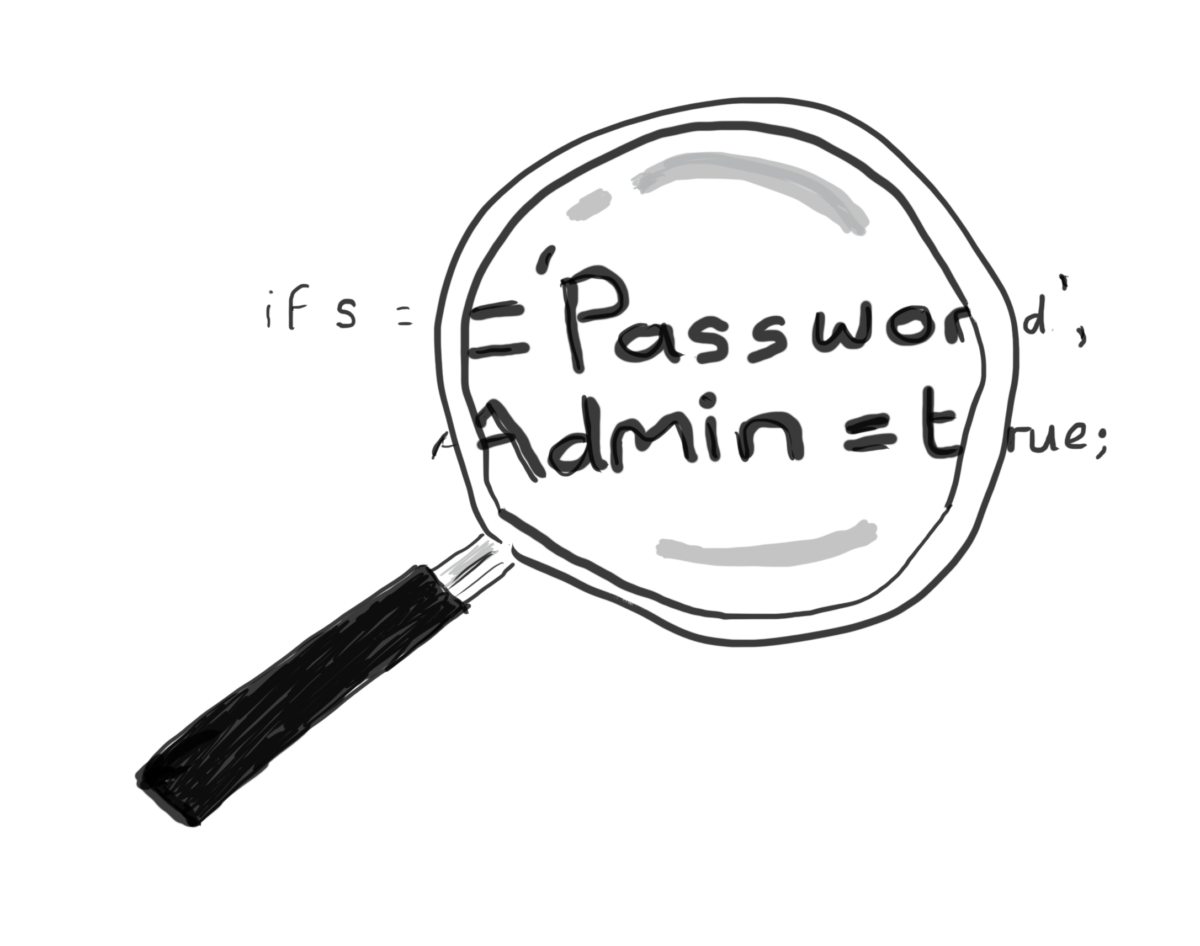
A question that comes up frequently in my capacity as a DevOps / Agile Security consultant is: how do we integrate security test automation into our environments. There is a lot of information on automated security testing tools, but unfortunately, the vast majority of it is written by the companies who produce and sell the tools. Their literature paints a very healthy picture of how all the tools are integrated. In September 2019, I attended a DevSecOps event in London in which a small number of application security testing vendors were invited along to talk about how they secure their…Continue readingSecurity test automation part 1: SAST
If you are using appsec tools in your pipeline you are probably asking what their benefits are. Typically, Static Application Security Testing (SAST) tools are prone to identifying false positives, which creates a lot of noise. The leadership questions why your tools, which were meant to reduce the number of vulnerabilities is reporting more vulnerabilities than ever. Furthermore, your Software Composition Analysis (SCA) tools appear to lack accuracy by reporting that all your code is at risk because you used a single dependency in one part of your application software. On the other hand, if you are scanning container images,…Continue readingAppsec tooling: value vs process